Technology Shouldn’t Be Scary!
Unfortunately, with new breaches constantly in the news, using technology with your business can be very scary. Many businesses don’t think about securing their systems until it is too late. While we can help with remediation as well, it is always cheaper to proactively protect your business from the beginning.
There is no such thing as 100% secure; but by following best practices and hardening your infrastructure, you can drastically reduce risk for your business. Learn about our 3-pronged approach to security services below!


Policy Development
Keeping your company secure starts with defining what needs to be protected. Each business is unique, and starting by defining what needs to be accomplished rather than focusing on a vague abstract notion of security helps to ensure that we are always moving in the right direction that helps the business rather than getting in the way of your business making money.
Control Implementation
Once we have policies in place, it is time to enforce them. Finding the right tools helps, but security isn’t just about having fancy tools, it’s about staying proactive and having qualified personnel managing the tools with specific goals in mind. We don’t try to fit you into a mold we’ve used for other businesses, we take the experience of working with multiple different layers and tools for security to figure out what will work best for your unique situation.
Forensics Services
Unfortunately many businesses don’t seek out help with information security until it is already too late and a breach has already occurred. Using our digital forensic incident response team, we can perform root cause analysis and get your business back on track as soon as possible. We also offer digital forensic consulting outside of incident response cases for legal teams and other cases requiring admissible evidence collection and processing.

About
Infosec Chicago
Our main goal is to reduce your information security risk in an easy and effective solution. Chances are, you already understand the importance of maintaining a secure environment, but you know that is often easier said than done. In the 2020 Data Breach Investigations Report, Verizon studied over 157,525 incidents and 108,069 breaches – that’s enough to keep any CIO or CISO up at night! Small and medium sized businesses often have the hardest time hardening their environment because they don’t have the resources to hire an entire information security team. That’s where Infosec Chicago comes in! We specialize in helping small to medium sized businesses with their information security needs. We recognize that each business is unique and that a one-size-fits-all approach to security will never succeed. Our solutions are custom tailored to your unique needs! If you have IT staff or a Managed Services Provider, we work with them to help them with the areas they aren’t comfortable with, rather than trying to take over every aspect of your IT infrastructure. If you don’t already have an existing IT support, we are happy to refer you to a security-conscious Managed Services Provider in your area that we can work with to provide you with a hardened and effortless IT infrastructure.
Constantly Evolving Strategies
Threat-actors are constantly evolving, why shouldn’t your protection be as well? By implementing tried and true security frameworks that support constant evolution, you can rest easy at night knowing your company isn’t the low-hanging fruit that threat-actors crave.
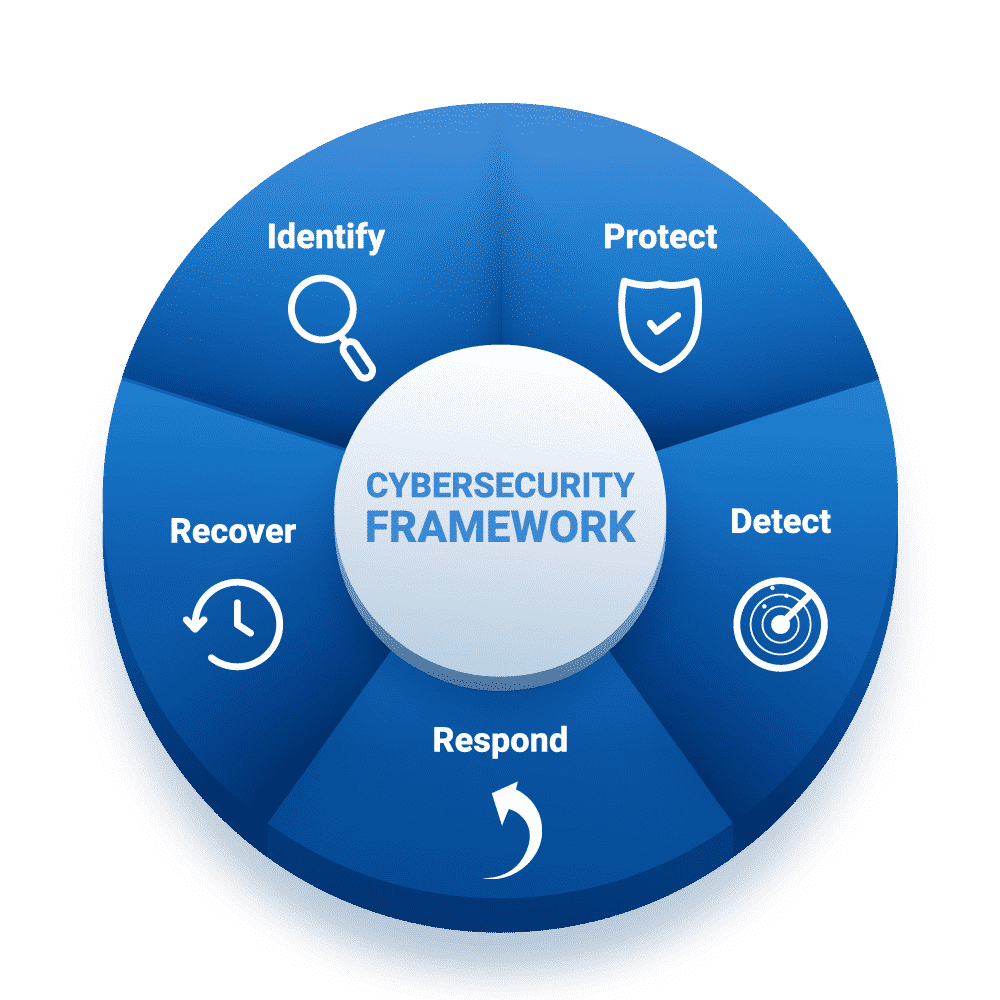
Our Services
We can assist across a multitude of security services, and we offer custom packages to supplement your existing IT team rather than requiring you to pay for services that you don’t need or your IT team already has covered.
Security Consulting
Proactive planning, policy development, incident response, managed services, penetration testing, and more starting at $250/hour.
Website Security
Security solutions built specifically for WordPress. Starting at $35/month, add on managed hosting for only $5/month more.
Web application penetration testing is also available!
Digital Forensics
We offer a variety of forensic services ranging from data recovery and forensic evidence acquisition, all the way to DFIR (Digital Forensics Incident Response) investigations, digital forensic analysis, and expert witness consulting.
Our Approach to Security
Our approach centers around user behavior. The information security community has said for years that one of the weakest links in any security system is the people using the system; however, rarely do the systems that we design take into account the user behavior. Instead we spin our wheels conducting phishing tests that we already know what the results are going to be before we even send the first email, only to turn around and say that the solution to this is user training. Of course user training is vitally important, but finding the right user training and building systems to account for “default” user behavior is just as (if not more) important.
Results of user-centric design
Not only does user-centric design improve the security posture of the organization, but it also improves the working environment. When IT stops blaming users and forcing them to work in ways that don’t come naturally, the culture drastically improves. Enterprise IT often has the “us vs. them” mentality – getting rid of this mentality and instead focusing on the user experience as part of the solution brings teams closer together.

Contact Us
(630) 412-1842
Get Started
Ready to get started? Book an appointment to speak with a security specialist!
